We provide advanced threat monitoring to detect and mitigate security risks across endpoints and mobile devices. Using continuous surveillance, anomaly detection, and behavioral analytics, we proactively identify suspicious activities before they escalate into security incidents. Our monitoring solutions ensure real-time visibility, rapid threat detection, and actionable intelligence to strengthen your organization’s cyber resilience.

Corporate Device Monitoring Solution
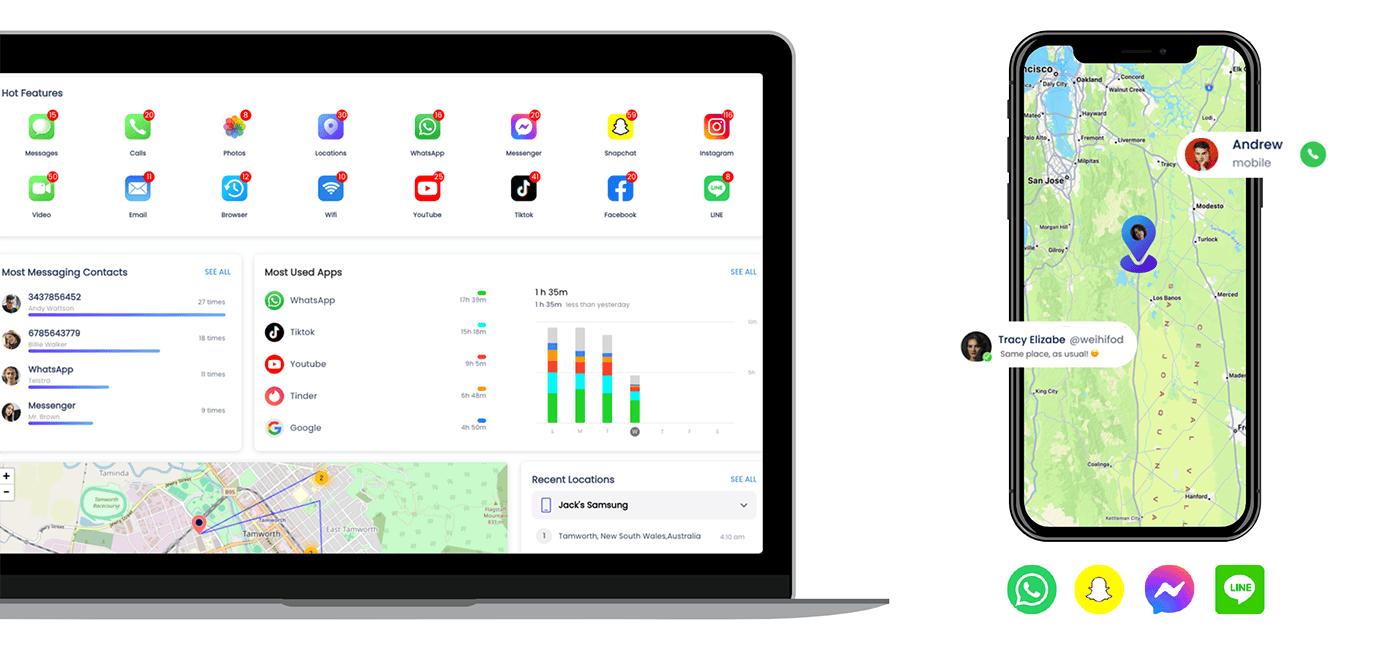
Monitoring Solutions
These are newly packaged devices equipped with pre-installed monitoring software.
Through intelligence operations, targets are guided to click on a link or attachment, which then activates the monitoring solution. This approach requires minimal interaction and is effective in various scenarios.
This method allows the target device to be exploited without any user interaction. This technology is exclusively available to governmental organizations and the public sector.
Support for identifying potential violations, unauthorized activities, or insider threats, helping maintain organizational integrity.
In-depth analysis of monitored data to uncover actionable insights into device behavior, communication patterns, and emerging risks. These insights support strategic decision-making and strengthen overall security posture.

Contact Us
Lets have a call to clear out all your questions about our services and the next steps towards implementation, we would love to know more about what are you looking for and knowing each other.